Microsoft has released security updates for two zero-day vulnerabilities: CVE-2022-41040, a server-side request forgery vulnerability, and CVE-2022-41082, which allows remote code execution. Collectively known as ProxyNotShell, the Exchange Server vulnerabilities have led to a spate of attacks linked to nation-state threat actors since late September.
The SUs address vulnerabilities responsibly reported to Microsoft by security partners and found through Microsoft’s internal processes. Our recommendation is to immediately install these updates to protect your environment.
Microsoft has released Security Updates (SUs) for vulnerabilities found in:
- Exchange Server 2013
- Exchange Server 2016
- Exchange Server 2019
NOTE: The November 2022 SUs contain fixes for the zero-day vulnerabilities reported publicly on September 29, 2022 (CVE-2022-41040 and CVE-2022-41082).
More details about specific CVEs can be found in the Security Update Guide.
The November 2022 SUs are available for the following specific versions of Exchange Server:
- Exchange Server 2013 CU23 (support ends in April 2023)
- Exchange Server 2016 CU22 and CU23
- Exchange Server 2019 CU11 and CU12
Because we are aware of active exploits of related vulnerabilities (limited targeted attacks), our recommendation is to install these updates immediately to be protected against these attacks.
Update installation
The following update paths are available:
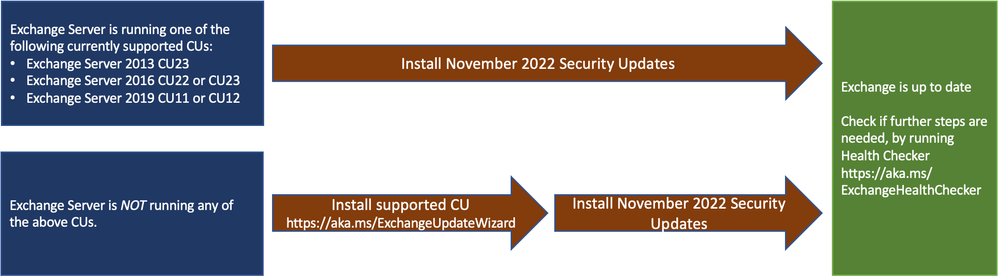
- Install the latest CU. Go to Exchange Update Wizard and choose your currently running CU and your target CU to get directions.
- Inventory your Exchange Servers to determine which updates are needed using the latest release of the Exchange Server Health Checker script. Running this script will tell you if any of your Exchange Servers are behind on updates (CUs, SUs, or manual actions). Re-run Health Checker after you install the SU to validate no further action is needed.
- If you encounter errors during or after installation of Exchange Server, run the SetupAssist script. If something does not work properly after updates, see Repair failed installations of Exchange Cumulative and Security updates.
Issues resolved by this release
- Delivery Report search from ECP might fail with IIS logs showing SEC_E_BAD_BINDINGS in a cross-site scenario after enabling Extended Protection
- Export-UMPrompt could fail with InvalidResponseException
Reach out to Messageware to improve Microsoft Exchange Server Security
If you are not protecting all the protocols used by your Exchange Server, you’re putting your company at a higher risk of a data breach.
Security incidents happen frequently. They cause disruption, loss of data and potentially risk the reputation of your company. However, if you implement these steps, you’re doing more than most other companies.
Have you heard about Messageware’s EPG that offers advanced Exchange Server security to protect organizations from a variety of logon and password attacks, as well as extensive real-time reporting and alerts of suspicious logon activity? Click here to learn more.
