Microsoft released security updates for Exchange Server on June 14, 2023. While no active threats are currently known to be exploiting these vulnerabilities, IT admins should prioritize patching them as soon as possible. One of the most critical vulnerabilities is a bypass of fixes for two Exchange Server remote code execution bugs. This vulnerability exists within the Command class and can be exploited by an attacker with an account on the Exchange server to execute code with SYSTEM privileges. IT admins should patch these vulnerabilities as soon as possible to protect their systems from attack.
Microsoft has released Security Updates (SUs) for vulnerabilities found in:
- Exchange Server 2016
- Exchange Server 2019
SUs are available for the following specific versions of Exchange Server:
More details about specific CVEs can be found in the Security Update Guide
Update installation
The following update paths are available:
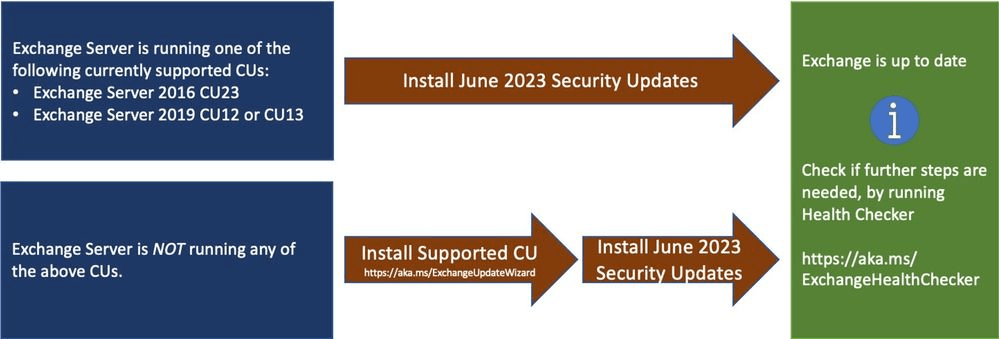
- Install the latest CU. Use the Exchange Update Wizard to choose your current CU and your target CU to get directions.
- Inventory your Exchange Servers to determine which updates are needed using the Exchange Server Health Checker script. Running this script will tell you if any of your Exchange Servers are behind on updates (CUs, SUs, or manual actions).
- Re-run the Health Checker after you install an SU to see if any further actions are needed.
- If you encounter errors during or after installation of Exchange Server, run the SetupAssist script. If something does not work properly after updates, see Repair failed installations of Exchange Cumulative and Security updates.
Issues resolved in this release
- “Object ‘<ServerName>’ couldn’t be found on ‘<DomainControllerName>'” error when trying to uninstall…
- Changing the permissions for Public Folders by using an Outlook client will fail with the following …
Description of the security update for Microsoft Exchange Server 2019: June 13, 2023 (KB5026261)
Microsoft Exchange Server Build Numbers for 2019
This security update rollup resolves vulnerabilities in Microsoft Exchange Server. To learn more about these vulnerabilities, see the following Common Vulnerabilities and Exposures (CVE):
- CVE-2023-28310 – Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE-2023-32031 – Microsoft Exchange Server Remote Code Execution Vulnerability
Issues that are fixed in this update
- Failure in Public Folder Quota email notifications
- Extended Protection doesn’t support Public Folder Client Permission Management through Outlook
- Microsoft Exchange Replication service crashes on host server
- Store Worker process crashes and returns “System.NullReferenceExceptions” multiple times per day
- Exchange won’t uninstall after the January Security Update (KB5022143) is applied
How to get and install the update
Method 1: Microsoft Update
This update is available through Windows Update. When you turn on automatic updating, this update will be downloaded and installed automatically. For more information about how to turn on automatic updating, see Windows Update: FAQ.
Method 2: Microsoft Update Catalog
To get the standalone package for this update, go to the Microsoft Update Catalog website.
Method 3: Microsoft Download Center
You can get the standalone update package through the Microsoft Download Center:
- Microsoft Exchange Server 2019 Cumulative Update 13 SU1- Download the package now
- Microsoft Exchange Server 2019 Cumulative Update 12 SU8- Download the package now
Description of the security update for Microsoft Exchange Server 2016: June 13, 2023 (KB5025903)
Microsoft Exchange Server Build Numbers for 2016
This security update rollup resolves vulnerabilities in Microsoft Exchange Server. To learn more about these vulnerabilities, see the following Common Vulnerabilities and Exposures (CVE):
- CVE-2023-28310 – Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE-2023-32031 – Microsoft Exchange Server Remote Code Execution Vulnerability
Issues that are fixed in this update
- Extended Protection doesn’t support Public Folder Client Permission Management through Outlook
- Microsoft Exchange Replication service crashes on host server
- Store Worker process crashes and returns “System.NullReferenceExceptions” multiple times per day
- Exchange won’t uninstall after the January Security Update (KB5022143) is applied
How to get and install the update
Method 1: Microsoft Update
This update is available through Windows Update. When you turn on automatic updating, this update will be downloaded and installed automatically. For more information about how to turn on automatic updating, see Windows Update: FAQ.
Method 2: Microsoft Update Catalog
To get the standalone package for this update, go to the Microsoft Update Catalog website.
Method 3: Microsoft Download Center
You can get the standalone update package through the Microsoft Download Center:
- Microsoft Exchange Server 2016 Cumulative Update 23 SU8 – Download the package now
Reach out to Messageware to improve Microsoft Exchange Server Security
If you are not protecting all the protocols used by your Exchange Server, you’re putting your company at a higher risk of a data breach.
Security incidents happen frequently. They cause disruption, loss of data and potentially risk the reputation of your company. However, if you implement these steps, you’re doing more than most other companies.
Have you heard about Messageware’s EPG that offers advanced Exchange Server security to protect organizations from a variety of logon and password attacks, as well as extensive real-time reporting and alerts of suspicious logon activity? Click here to learn more.
