Microsoft has released Security Updates (SUs) for vulnerabilities found in:
- Exchange Server 2019
- Exchange Server 2016
SUs are available for the following specific versions of Exchange Server:
The October 2023 SUs address vulnerabilities responsibly reported to Microsoft by security partners and found through Microsoft’s internal processes. Although we are not aware of any active exploits in the wild, our recommendation is to immediately install these updates to protect your environment.
This security update rollup resolves vulnerabilities in Microsoft Exchange Server. To learn more about these vulnerabilities, see the following Common Vulnerabilities and Exposures (CVE):
Issues that are fixed in this update
- Extended Protection causes Outlook for Mac not to update the OAB
- Details Templates Editor fails and returns BlockedDeserializeTypeException
- Users in account forest can’t change expired password in OWA in multi-forest Exchange deployments after installing August 2023 SU
CVE-2023-21709 now has a better solution: install update for CVE-2023-36434
During the release of August 2023 SUs, we recommended to use a manual or scripted solution and disable the IIS Token Cache module as a way of addressing CVE-2023-21709. Today, Windows team has released the IIS fix for root cause of this vulnerability, in the form of fix for CVE-2023-36434. We recommend installing the IIS fix after which you can re-enable Token Cache module on your Exchange servers.
If you did not do anything to address CVE-2023-21709 yet:
- Install update for CVE-2023-36434 on all your Exchange Servers.
If you have followed our August 2023 recommendation and disabled the Token Cache module (either by using single-line command or our CVE-2023-21709.ps1 script), or want to address possible performance concerns you have seen since disabling the module, do the following:
- Install update for CVE-2023-36434 on all your Exchange Servers.
- Re-enable IIS Token Cache module by doing one of the following:
- To enable Token Cache module on individual server only, run the following from the elevated PowerShell window:
New-WebGlobalModule -Name “TokenCacheModule” -Image “%windir%\System32\inetsrv\cachtokn.dll”
- To enable Token Cache module on all servers in the organization (after Windows Updates were installed), you can use our CVE-2023-21709.ps1 as Administrator in Exchange Management Shell (EMS):
- .\CVE-2023-21709.ps1 -Rollback
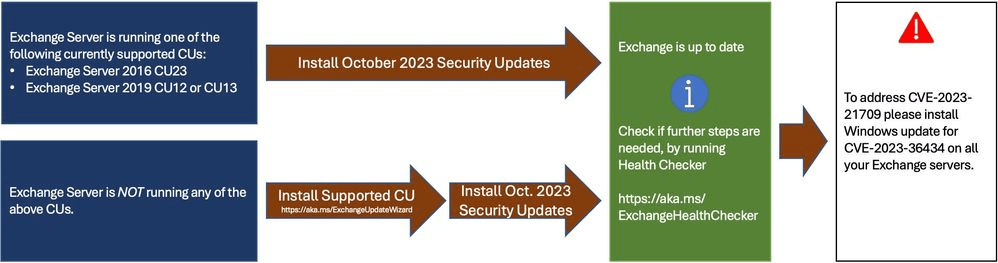
- Install the latest CU. Use the Exchange Update Wizard to choose your current CU and your target CU to get directions.
- Inventory your Exchange Servers to determine which updates are needed using the Exchange Server Health Checker script. Running this script will tell you if any of your Exchange Servers are behind on updates (CUs, SUs, or manual actions).
- Re-run the Health Checker after you install an SU to see if any further actions are needed.
- If you encounter errors during or after installation of Exchange Server, run the SetupAssist script. If something does not work properly after updates, see Repair failed installations of Exchange Cumulative and Security updates.
How to get and install the update
Method 1: Microsoft Update
This update is available through Windows Update. When you turn on automatic updating, this update will be downloaded and installed automatically. For more information about how to turn on automatic updating, see Windows Update: FAQ.
Method 2: Microsoft Update Catalog
To get the standalone package for this update, go to the Microsoft Update Catalog website.
Method 3: Microsoft Download Center
You can get the standalone update package through the Microsoft Download Center.
- Microsoft Exchange Server 2019 Cumulative Update 13 SU3- Download the package now
- Microsoft Exchange Server 2019 Cumulative Update 12 SU10- Download the package now
- Microsoft Exchange Server 2016 Cumulative Update 23 SU10- Download the package now
Reach out to Messageware to improve Microsoft Exchange Server Security
If you are not protecting all the protocols used by your Exchange Server, you’re putting your company at a higher risk of a data breach.
Security incidents happen frequently. They cause disruption, loss of data and potentially risk the reputation of your company. However, if you implement these steps, you’re doing more than most other companies.
Have you heard about Messageware’s EPG that offers advanced Exchange Server security to protect organizations from a variety of logon and password attacks, as well as extensive real-time reporting and alerts of suspicious logon activity? Click here to learn more.
