A sophisticated keylogger has been found embedded in the main login page of Microsoft Exchange Servers, stealing account credentials from unsuspecting users. The malicious code was discovered by Positive Technologies’ Expert Security Centre (PT ESC) during an incident response operation. The keylogger records usernames and passwords entered on the Exchange login page and stores them in a file accessible via a special path on the internet. This has allowed the attackers to stealthily collect sensitive login information from their victims.
Attack Mechanism
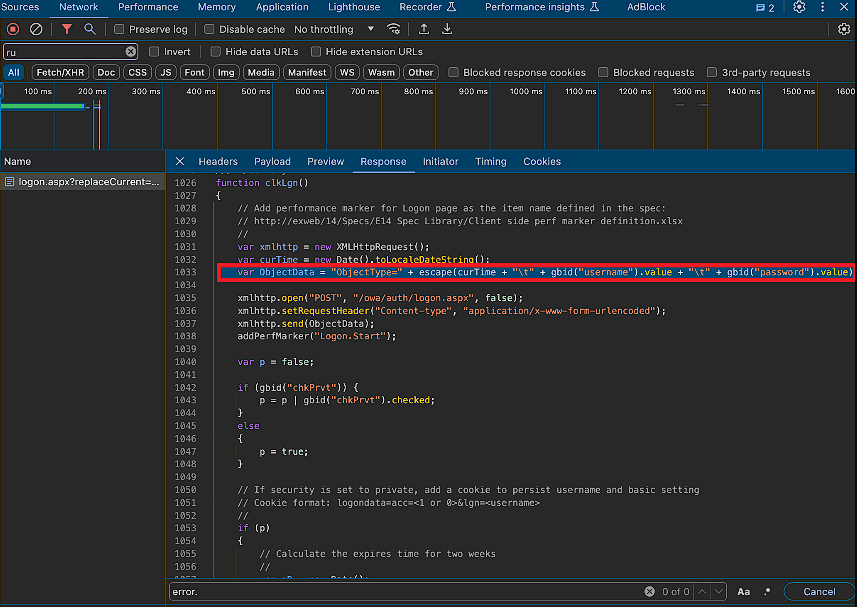
To inject the keylogger, the threat actors exploited the ProxyShell vulnerability (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207), a set of well-known security flaws in Microsoft Exchange Servers. By leveraging these vulnerabilities, the attackers were able to add the keylogger code to the server’s main page, specifically within the clkLgn() function.
var ObjectData = "ObjectType=" + escape(curTime + "\t"
+ gbid("username").value + "\t" + gbid("password").value)
+ "&uin=" + Math.random().toString(16).substring(2);
Additionally, the logon.aspx file was modified to process the captured credentials and redirect them to a file accessible from the internet. PT ESC has identified over 30 victims so far, predominantly government agencies but also including banks, IT companies, and educational institutions. The affected organizations are located across Africa and the Middle East, in countries such as Russia, UAE, Kuwait, Oman, Niger, Nigeria, Ethiopia, Mauritius, Jordan, and Lebanon. The earliest known compromise dates back to 2021.
Mitigations
To mitigate this threat, organizations running Microsoft Exchange Server are advised to:
- Update to the latest version of Exchange Server
- Check for signs of compromise by searching for the keylogger code on the server’s main page
- Ensure all known vulnerabilities, especially ProxyShell, are patched promptly
- Monitor server logs for anomalous activity and access attempts
- Implement strong security controls like multi-factor authentication
This incident highlights the critical importance of keeping systems up-to-date, as attackers continue to exploit known vulnerabilities to compromise even widely used enterprise software. Organizations must remain vigilant and proactively secure their environments to safeguard against evolving cyber threats.
Stop attacks on Exchange Server with Messageware Z-Day Guard
Messageware Z-Day offers next generation threat hunting and protects Microsoft Exchange servers against zero day attacks. Z-Day detects changes to the environment that indicate the dropping of Command and Control (C&C) web shells. C&C web shells commonly reach out to the internet, enabling remote access to your network.
Z-Day is a server protection solution focused on detection, alerting, and response (MDR/MDAR) to zero-day attacks and server penetrations. Messageware Z-Day actively protects servers using embedded monitoring technology that cannot be turned off by malicious software.
Contact us to start your free trial.

