Microsoft has re-released the November 2024 SUs for Exchange Server. The original release of these SUs (released on 11/12/2024) introduced an issue with Exchange Server transport rules stopping after a certain amount of time in some environments. The re-released SUs resolve this issue. To help you understand how to move forward, refer to this post.
The November 2024 SUs address vulnerabilities responsibly reported to Microsoft by security partners and found through Microsoft’s internal processes. Although we are not aware of any active exploits in the wild, our recommendation is to immediately install these updates to protect your environment.
Microsoft has released Security Updates (SUs) for vulnerabilities found in:
- Exchange Server 2019
- Exchange Server 2016
SUs are available for the following specific versions of Exchange Server:
These vulnerabilities affect Exchange Server. Exchange Online customers are already protected from the vulnerabilities addressed by these SUs and do not need to take any action other than updating any Exchange servers or Exchange Management tools workstations in their environment.
More details about specific CVEs can be found in the Security Update Guide (filter on Server Software under Product Family).
The November 2024 Exchange Server Security Updates introduce three significant improvements:
AMSI Integration Enhancement
The Exchange Server AMSI (Antimalware Scan Interface) integration now offers expanded capabilities for message body scanning. This feature remains disabled by default but can be enabled per protocol. Microsoft recommends a gradual rollout, starting with a subset of services, due to potential performance impacts. Please see the documentation for more information.
Security Enhancement
A new security feature has been implemented to address vulnerability CVE-2024-49040. This feature detects non-RFC 5322 compliant P2 FROM headers in incoming emails. The P2 FROM header is the sender information displayed in the recipient’s email client, such as Outlook. Please see the documentation for more information.
ECC Certificate Improvements
The update enhances ECC (Elliptic Curve Cryptography) certificate support with two key changes:
- ECC certificates can now be used on Edge Transport servers
- Support for POP and IMAP service binding
The implementation method has changed from using New-SettingOverride to requiring a registry value configuration. Please see the documentation for more information.
Update installation
The following update paths are available:
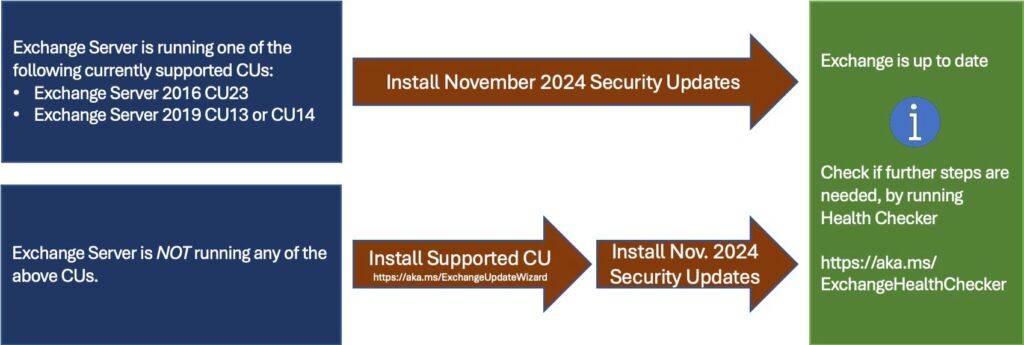
- Install the latest CU. Use the Exchange Update Wizard to choose your current CU and your target CU to get directions.
- Inventory your Exchange Servers to determine which updates are needed using the Exchange Server Health Checker script. Running this script will tell you if any of your Exchange Servers are behind on updates (CUs, SUs, or manual actions).
- Re-run the Health Checker after you install an SU to see if any further actions are needed.
- If you encounter errors during or after installation of Exchange Server, run the SetupAssist script. If something does not work properly after updates, see Repair failed installations of Exchange Cumulative and Security updates.
Strengthen Your Server Security with Messageware
Data breaches have increased by 72%, servers are compromised in under 90 minutes. Ensure you have multiple layers of security software protecting your Windows Servers.
Messageware offers powerful security solutions, including:
Z-Day Guard for All Windows Servers: Next-gen server protection, providing detection, alerting, and response (MDR) to zero-day and server penetration cyber-attacks. Leverages embedded monitoring technology that cannot be turned off by malicious software. No need to research complicated deployments and no learning curve to install and manage.
EPG Guard for Exchange Servers: Real-time security stops AD account lockouts, eliminates brute force password attacks, provides intelligent GEO blocking, and prevents Exchange Server vulnerability probing. Enhance security through real-time collection and analysis of logon information, with advanced reporting, threat detection, and security controls.
Don’t leave your critical infrastructure vulnerable, be proactive and stay ahead of evolving threats.
