
Who’s probing your Exchange Server?
Today’s systems reveal more information to the internet than intended. If you have an internet facing Exchange Server, it is being probed to discover its specifications, vulnerabilities, and weaknesses.
Hackers
Hackers probe Exchange Servers to identify weaknesses or misconfigurations that can be exploited for unauthorized access, data theft, or launching command and conquer attacks. This poses a significant risk to your organization’s sensitive information and operations.
Internet of Things (IoT) Indexers
Companies like Shodan collect internet intelligence data, or more simply, they catalogue the internet for connected devices including Exchange Servers. These catalogue engines scan Exchange Servers for all available metadata and provide the public with tools to report on the discovered content.
For example, Shodan simplifies the process of searching for Microsoft Exchange Servers with a variety of filters and reveals all collected data. While this capability can help companies identify unpatched and vulnerable servers, it is also used by attackers to find targets for known exploits.
Vulnerable Exchange Servers scan results on the Shadowserver Dashboard, September 2023:
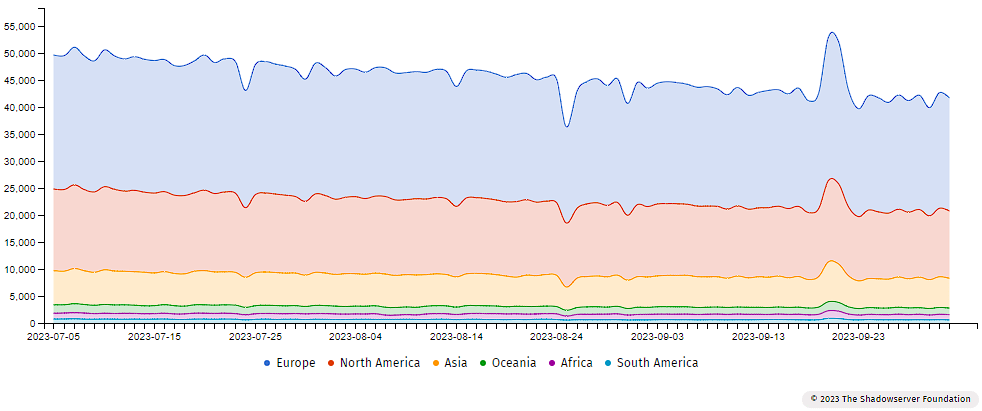
Five probing systems that catalogue Exchange Server data:
- Shodan is like Google, but for Internet of Things (IoT) devices. While Google indexes the websites on the world wide web and the content on these websites, Shodan indexes devices directly connected to the internet.
- ShadowServer Is a non-profit security organization that gathers and analyzes data on malicious Internet activity.
- Censys is a leading Internet Intelligence Platform for Threat Hunting and Exposure Management.
- ZoomEye is a Chinese based cyberspace search engine.
- IVRE is an open-source framework for network recon. It relies on open-source well-known tools (Nmap, Masscan, ZGrab2, ZDNS and Zeek (Bro)) to gather data and network intelligence.
What are Exchange Servers being probed for?
Attackers are looking to exploit unpatched Exchange Servers. There are many aspects of unpatched on-premises Exchange environments that are valuable to bad actors looking to exfiltrate data or commit other malicious acts.
- Exchange Server services: ActiveSync, OWA, Autodiscover, ECP, EWS, MAPI/HTTP, MAPI/RCP, OAB, and Rest
- Exchange Server version numbers: Identifying a server’s version number allows hackers to exploit any known vulnerabilities associated with that particular version. As new patches are released monthly to combat zero-day vulnerabilities, out-of-date software poses a significant risk to overall security.
How Attackers Use Publicly Available Internet Scanners
Using the search feature at www.shodan.io, it’s easy to find out how many Microsoft Exchange 2013 and 2016 installations are exposed on the web:
X-AspNet-Version http.title:”Outlook” –”x-owa-version
Or, how many Exchange 2010 Servers are exposed to the web:
"x-owa-version" "IE=EmulateIE7" http.favicon.hash:442749392
Shodan can also be used to locate servers with specific build numbers or CVE vulnerabilities.
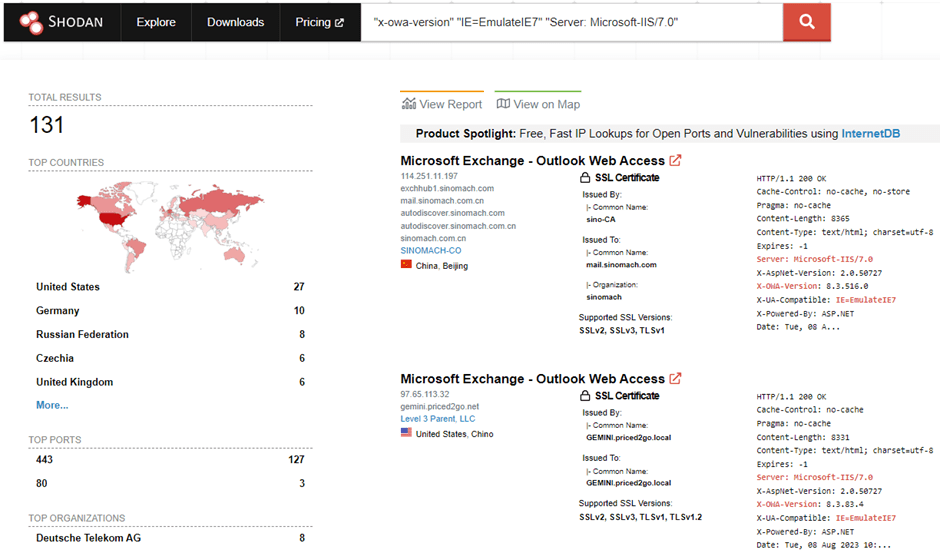
Surprisingly, there are still results for Exchange Server 2007 whose support ended April 11th, 2011:
"x-owa-version" "IE=EmulateIE7" "Server: Microsoft-IIS/7.0"
Are these systems legal?
It may seem counter intuitive that systems that are unrelated to your business can connect without authorization to your servers, gather details about ports, software versions, geographical location, etc., and publicly share this sensitive data. However, these scanning services are not illegal. For considerations on the legality of scanning, refer to these two articles: nmap, rapid7.
How to: Block IoT scanners like Shodan, Censys, Shadowserver
Protect your Exchange Server against internet IoT port scanners and web crawlers by creating a drop rule on your firewall. Add the following IP addresses to the drop rule:
| Shodan | Censys | ShadowServer |
|---|---|---|
| .census1.shodan.io .census2.shodan.io .census3.shodan.io .census4.shodan.io .census5.shodan.io .census6.shodan.io .census7.shodan.io .census8.shodan.io .census9.shodan.io .census10.shodan.io .census11.shodan.io .census12.shodan.io .atlantic.census.shodan.io .pacific.census.shodan.io .rim.census.shodan.io .m247.ro.shodan.io .pirate.census.shodan.io .ninja.census.shodan.io .border.census.shodan.io .burger.census.shodan.io | 162.142.125.0/24 167.94.138.0/24 167.94.145.0/24 167.94.146.0/24 167.248.133.0/24 2602:80d:1000:b0cc:e::/80 2620:96:e000:b0cc:e::/80 Additionally, our HTTP-based scans use a Censys specific user agent, which can be used to filter requests from our scanners. | To opt out of ShadowSever scanning activity email: dnsscan@shadowserver.org and list the specific CIDRs you would like to have removed. (You’ll need to prove that you’re the verifiable owner of these CIDRs.) |
Defeat Probing and Malicious Attacks with Messageware EPG
Exchange Server services are not protected, even with 2FA/MFA for end-users. Hackers and bots are constantly probing your Exchange Server to find vulnerabilities. Brute force password guessing, password spraying, widespread AD lockouts, and zero-day attacks cause significant damage and create havoc in your support center.
Messageware Exchange Protocol Guard (EPG) provides advanced intelligence and control for Microsoft Exchange Servers by monitoring potential risks from attacks that target Exchange services and protocols. Enhance your on-premises Microsoft Exchange security with real-time threat detection and security controls.
EPG proactively secures Exchange Server services: Outlook Web, EWS, ECP, ActiveSync, Autodiscover, OAB, MAPI/RCP, MAPI/HTTP and REST.
References:
Shodan: https://blog.checkpoint.com/research/check-point-threat-alert-shodan/
Censys: https://support.censys.io/hc/en-us/articles/360038378552-Frequently-Asked-Questions
Shadowserver: https://www.shadowserver.org/faq/can-i-opt-out-of-your-scanning-activity/
